MyPlace/MyAir support for IoT VLAN
I've upgraded my home network to use separate VLANs for security, specifically keeping IoT devices and guests off my main network.
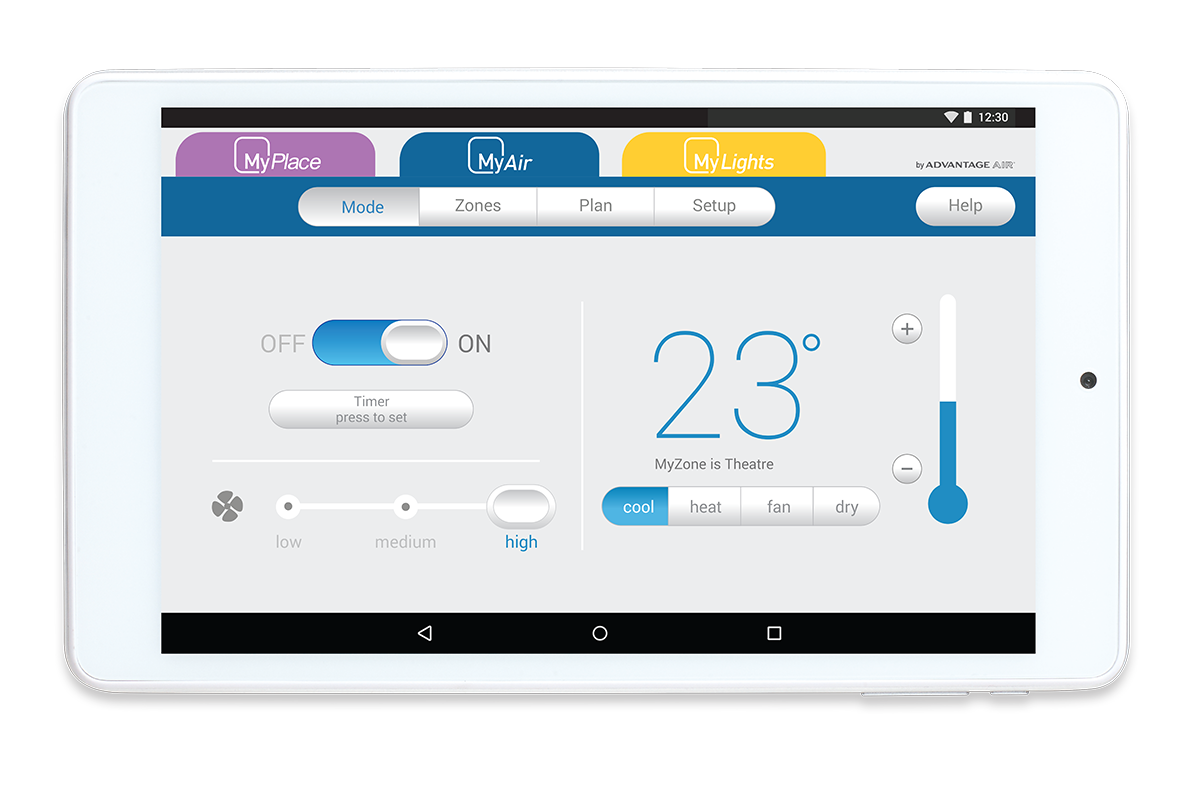
One device that did not "just work" is the air conditioning controller tablet from Advantage Air. While the controller device was functional, I could not get the mobile app MyPlace to connect from the source (secure) VLAN to the IoT VLAN.
To figure this out I had to do some Wireshark analysis. Not only did I figure out how to get MyPlace to work across VLANs, but I also discovered how to improve the app connection reliability.
When you start the MyPlace app (the client), it needs to make a connection to the controller tablet (the server), so that it can retrieve information, and allow updates.
Discovery protocol and connection reliability fix
The app doesn't provide any mechanism to configure the network, instead it automatically attempts to discover the controller. This is achieved by making a HTTP connection request to TCP port 2025 on every IPv4 address in the local network.Since it only connects to local subnet network addresses, it is not possible for the MyPlace app to discover the device in another network. Furthermore, depending on the network configuration it may need to scan up to 254 network addresses before the correct address is found. I've found that the Android app will often timeout and give an unhelpful screen with the status code AA46.
The best strategy to prevent timeout issues is to assign a static IP with a low device number, or alternatively consider changing your LAN to use a smaller subnet size (/23, /22).
VLAN communication fix
If the client app only communicates to IP addresses in the client VLAN, then I will need to use a "proxy" to redirect requests to the server VLAN. It doesn't even need to be anything fancy - just something to forward the TCP request/reply packets.
You will need to configure the controller tablet (server) to use a static IP within the IoT VLAN. Then in the client VLAN you will need host a forwarding proxy. I ended up with running a utility on my Synology NAS - which is in the same secure network as the client app.
Now there's a few different ways of forwarding TCP requests, using ssh, iptables, or utilities like netcat and socat. I found the simplest and most reliable was to use socat - adapting these instructions.
The socat utility is not installed by default on my NAS, so I used ipkg to install. Then configured a scheduled task to run at NAS boot up. Just substitute DestIP with the actual IP address (static IP) of your controller tablet.
/opt/bin/socat tcp-listen:2025,reuseaddr,fork tcp:DestIP:2025
For firewalling between the two VLANs, I allow all packets from Secure to IoT, but only allow TCP replies from IoT to Secure.
I've found the app communicates reliably over this inter-VLAN connection. However if you experience connection timeouts then you might need to use a low IP address number for the forwarding proxy.
I hope that helps you out.



Comments
Thanks very much for the details. I am a security conscious guy with a separate IOT network for crap devices like this. For those who need a bit more details, I found this helpful to get OPKG/IPKG installed on my Synology NAS DS220+ so i could then install socat:
https://community.synology.com/enu/forum/1/post/127148
I installed OPKG instead of IPKG.
Once you have IPKG or OPKG installed, then install SOCAT:
sudo /opt/bin/opkg install socat
To create the task to run SOCAT at boot up go to Control Panel > Task Scheduler > Create Triggered Task > User Defined Script.